Types of Authentication
Common Authentication Methods
1. Single Factor Authentication
- Simplest and common form of authentication
- Also known as “Primary authentication”
- Requires only 1 authentication mentod like password , pin , etc
Evaluation
- Usability and setup : 5/5
- Security : 2/5 (Poor)
2. 2-Factor Authentication
- Better than single factor authentication in terms of security
- 2FA can be OTP coming in mobile devices (common in these days)
- Requires only 1 authentication mentod like password , pin , etc
Evaluation
- Usability and setup : 3.5/5
- Security : 3.5/5 (Better)
3. Multi-factor Authentication (MFA)
- Sophisticated authentication mechanism which can leverage 2 or more factors to grant user access to the system
- We can find in scenarios where we put our credential , get OTP in mobile device and finally answer secret questionaire.
Evaluation
- Usability and setup : 3/5
- Security : 5/5 (Best)
Common Authentication Protocols
1. Password Authentication Protocol (PAP)
Evaluation
- Usability and setup : 5/5
- Security : 1/5 (Poor) In this process , it requires a username and password combination to access any system, which validates the provided credentials.
2. Challenge Handshake Authentication Protocol (CHAP)
- Usability and setup : 3/5
- Security : 4/5 CHAP is an identity verification protocol that verifies a user to a given network with a higher standard of encryption using a three-way exchange of a “secret.”
3-way exchange of secret are as follows :
- Local router sends a “challenge” to the remote host, which then sends a response with an MD5 hash function.
- The router matches against its expected response (hash value)
- Depending on whether the router determines a match, it establishes an authenticated connection—the “handshake”—or denies access.
3. Extensible Authentication Protocol
- Supports various types of authentication
- EAP is one of the highesy level of security for wireless communication
- It connects users to the access point that requests credentials, confirms identity via an authentication server, and then makes another request for an additional form of user identification to again confirm via the server—completing the process with all messages transmitted, encrypted.
- Usability and setup : 3/5
- Security : 5/5
API Authentication Protocols
1. HTTP Basic Auth
- In this case, user can provide username and password to prove their authentication.
- Does not require cookies, session ID’s, or login pages because it leverages the HTTP header itself.
- Usability and setup : 5/5
- Security : 1/5
2. API Keys
- A key is generated the first time a user attempts to gain authorized access to a system through registration.
- Next, the API key gets associated with a secret token, and is submitted alongside requests going forward.
- When the user attempts to re-enter the system, their unique key is used to prove that they’re the same user as before.
- Reliable and fast but can be misused many times
3. OAuth
- Most secure methods of API authentication,
- Supports both authentication and authorization.
- OAuth allows the API to authenticate by establishing scope, and can access the system or resource requested.
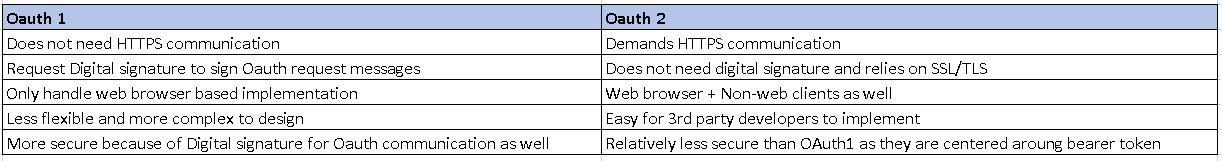
OAuth 1 vs OAuth 2
Please look into Okta’s playbook for authentication for more details - here is the link